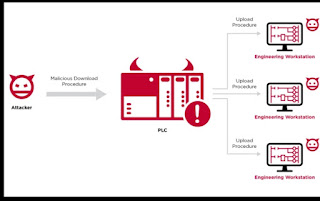
Team82 has developed a novel attack that weaponizes programmable logic controllers (PLCs) in order to exploit engineering workstations and further invade #OT and enterprise networks. They’re calling this the Evil #PLC Attack.
The attack targets engineers working every day on industrial networks, configuring and troubleshooting #PLCs to ensure the safety and reliability of processes across critical industries such as utilities, electricity, water and wastewater, heavy industry, manufacturing, and automotive, among others.
The Evil #plc Attack research resulted in working proof-of-concept exploits against seven market-leading automation companies, including Rockwell Automation, Schneider Electric, GE, B&R, XINJE, OVARRO, and Emerson.
The Evil PLC Attack turns the PLCs into the tool rather than the target. By weaponizing one PLC, an attacker may in turn compromise the engineer’s workstation, which is the best source for process-related information and would have access to all the other PLCs on the network. With this access and information, the attacker can easily alter the logic on any PLC.
The trick would be to lure an engineer to connect to a compromised PLC; the quickest way is to cause a fault on the PLC. That is a typical scenario an engineer would respond to, and connect using their engineering workstation application as a troubleshooting tool.
Full report here https://claroty.com/team82/blog/evil-plc-attack-using-a-controller-as-predator-rather-than-preyhttps://claroty.com/team82/blog/evil-plc-attack-using-a-controller-as-predator-rather-than-prey
#plcprogramming #plcscada #otsecurity #cyber #scada #ot #itsecurity #cybersecurity #redteam #pentest #pentesting #hacking #hackers #coding #malware
#utilities #electricity #water #wastewater #heavyindustry #manufacturing #automotive









0 comments:
Post a Comment